Are CFOs spending too much on cybersecurity? At first glance, it might sound like a ridiculous question. Cyber-attacks are growing year-on-year in Australia while high-profile ransomware attacks like the one on Medibank show how devastating the consequences can be. Cybersecurity should be a major priority for organisations of all sectors and sizes.
You’re out of free articles for this month
There’s just one problem, though: record cybersecurity spending hasn’t translated into fewer cyber incidents.
In 2020, Australians spent $5.6 billion on cybersecurity products and services, according to industry body AustCyber. If we are spending more than ever on cybersecurity, then why is cyber-crime still on the rise?
Especially with many businesses facing economic headwinds, CFOs need to be asking this question.
Part of the answer might come back to their own approaches to security. Here’s why – along with the steps you can take to protect your organisation.
Cyber criminals have a single-minded focus
According to a recent Annual Cyber Threat Report by the Australian Cyber Security Centry, over 83 per cent of all reported cyber-crimes were financially motivated. Meanwhile, cybersecurity practices tend to focus on protecting data and associated ICT systems.
In other words, a lot of cybersecurity products exclusively work to protect the organisation’s systems and data – and that’s definitely important. But, at the end of the day, most cyber-criminals just want your money.
Let’s look at a practical example. Business email compromise (BEC) attacks are common, costing Australians over $98 million last financial year. This tactic sees scammers gaining access to an executive’s email account and using it to send instructions to accounts payable (AP) staff to make illegitimate payments.
Your cybersecurity strategy should prevent scammers from accessing the email account in the first place, but no cybersecurity strategy is 100 per cent foolproof. And there are even fewer guarantees when it comes to your suppliers’ security practices, which means AP teams also need to be on guard against scammers who’ve taken control of trusted contacts’ accounts.
Lastly, new artificial intelligence capabilities and deep fake technology are making it easier than ever to fake an identity. Cyber-criminals are wielding increasingly sophisticated technologies and tactics against employees and without a fresh approach from leaders, the chances that workers will fall victim increase daily.
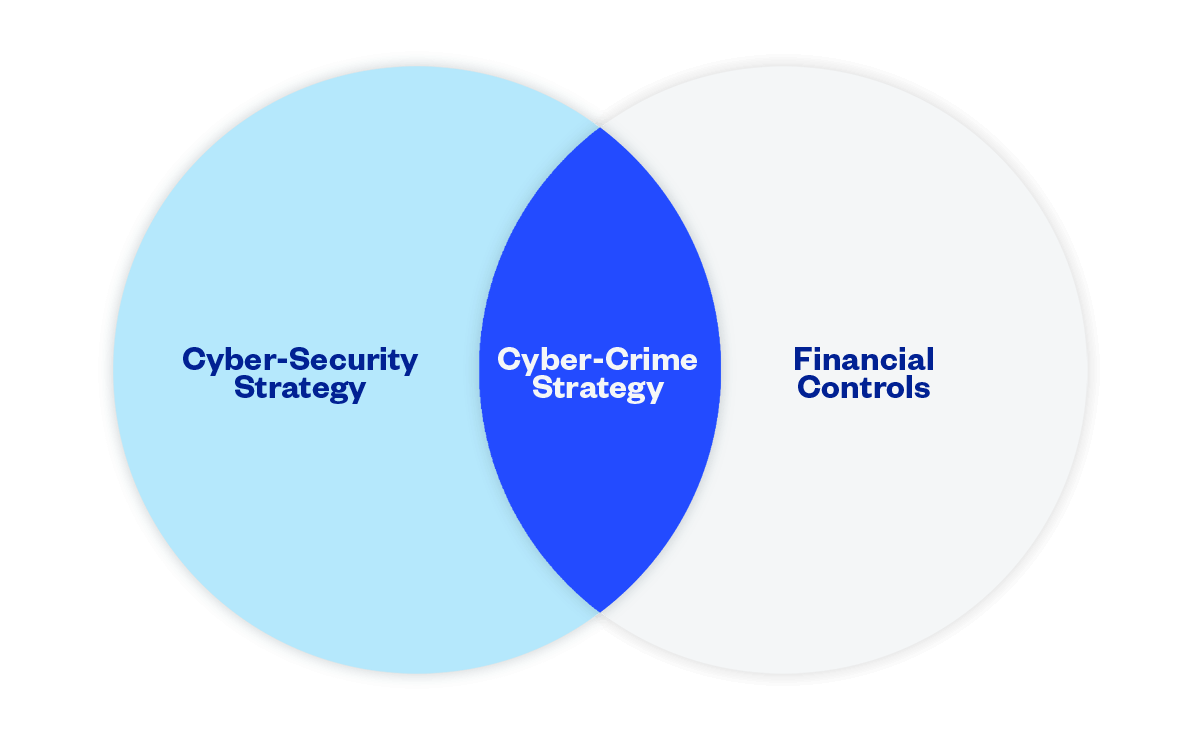
A CFO-led cyber-crime strategy
In our BEC example, it’s clear how cyber-criminals can exploit gaps between IT and finance. Luckily, a dedicated cyber-crime strategy can help financial leaders seal off those gaps and thwart scammers as they work toward their ultimate goal of stealing money.
A cyber-crime strategy shares some elements of a cybersecurity strategy – for example, it employs strong user access controls. But a cyber-crime strategy brings together elements of both a cybersecurity strategy and a company’s financial controls. It recognises the importance of information security practices while also acknowledging the importance of robust financial controls, such as segregation of duties.
To get a little more granular, a cyber-crime strategy has five key elements:
- Training
- Internal controls
- Culture
- Technology
- Pressure testing
All of these elements work together to unite financial controls with a cybersecurity strategy, ensuring that an organisation has much stronger defences if and when a cyber-criminal lands in an AP employee’s inbox.
As the longtime guardians of their businesses’ finances, CFOs are in the best position to establish and maintain this strategy. Financial crimes and fraud attempts are rapidly changing as technology continues to complicate the overall threat landscape – there’s no longer a clear distinction between traditional fraud and cyber-fraud.
So, while IT and security leaders play an indispensable role, CFOs will have to ensure their approaches evolve alongside this new threat landscape. And that starts with a cyber-crime strategy.
Gerard Mondaca is community security manager at Eftsure.

 Login
Login







